Cloud Security at Ellucian
Security and availability are top priorities at Ellucian. Our global team of information security and cloud experts work 24/7 to keep our customers’ data private and secure. Learn more about our key infosec practices in our cloud security white paper.
Risk and Compliance
Ellucian aligns itself with industry best practices and complies with key standards and regulations. Ellucian's information security program is modeled on the ISO 27001 Information Security Management System framework, and we are compliant or align with several international industry security standards and regulations for cloud platform solutions.
Each year, an independent audit firm conducts our annual Service Organization Control (SOC) audits. The SOC1, SOC2 Type II, and SOC 3 reports are available to customers.
Ellucian Cloud Services achieved its ISO27001:2013 certification in 2021. The ISO certification demonstrates Ellucian's commitment to security across its products and cloud services and demonstrate the effectiveness of our security controls. Certification is achieved following a rigorous independent audit of our conformity to the ISO standard.
SOC reports, ISO27001 certification, and other frequently requested security documents are available in the Ellucian Trust Center.
- SSAE 18 SOC1, 2, and 3 reporting
- ISO 27001:2013
- Cloud Security Alliance (CSA)
- EDUCAUSE Higher Education Cloud Vendor Assessment Tool (HECVAT)
- Payment Card Industry Data Security Standard (PCI DSS)
- NIST 800-171
- Cyber Essentials Basic (UK)



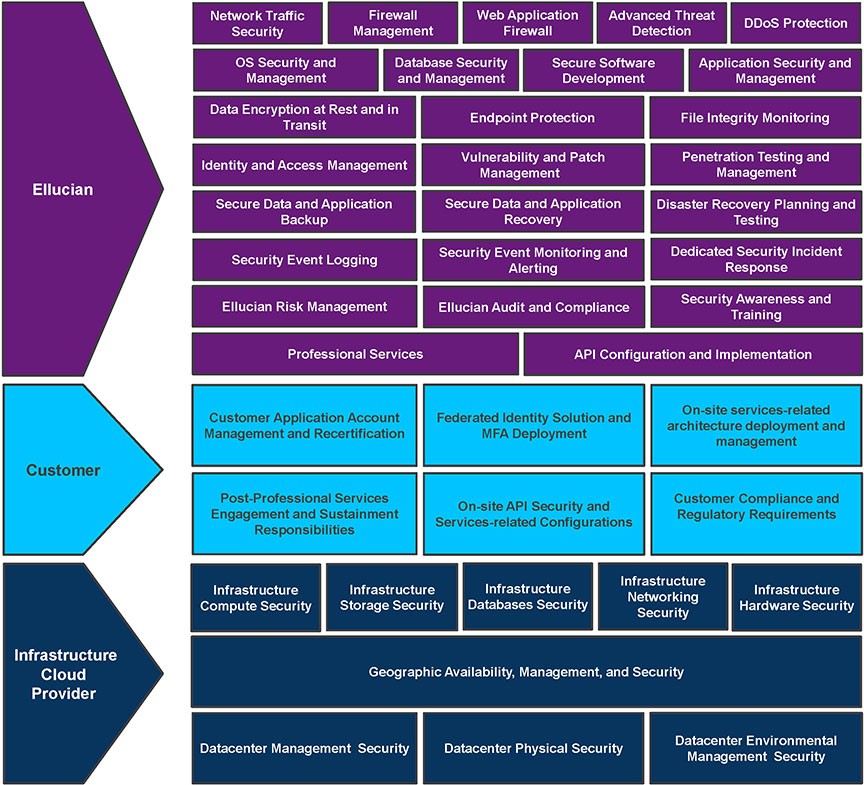
Ellucian Cloud Shared Security Responsibility Matrix
Information Security is a shared responsibility between Ellucian and our customers. As a customer moves towards a full Software-as-a-Service (SaaS) solution, more — but not all — security tasks will be handled by Ellucian. The following diagram depicts the areas of responsibility between the customer and Ellucian for a SaaS deployment as well as an overview of security services provided for Ellucian SaaS solutions.
Privacy
Ellucian is committed to maintaining your confidence and trust.
- Read our full privacy notice at ellucian.com/privacy.
Incident Response
Ellucian has a detailed incident response plan in place in the event of a security incident, and 24x7 monitoring of its security systems and alerts.
- Aligns with U.S. Computer Emergency Readiness Team (US CERT)
- Aligns with National Institute of Standards and Technology (NIST)
Threat Monitoring
Ellucian utilizes a defense-in-depth approach to security for its cloud service offerings. Ellucian works hard to earn your trust—and keep it.
- Amazon Web Services (AWS) Inspector and Tenable vulnerability management
- AWS Guard Duty threat monitoring
- Google Rapid Response
- AWS Web Application Firewalls
- AWS Shield DDoS protection
- Antivirus/anti-malware
- Endpoint protection
- Network security groups
- Splunk SIEM event monitoring and alerting
Application Security Feature Sheets
Feature Sheets provide an overview of our appsec and development processes, current practices, and industry standards used to secure each application and data—from robust documentation and authentication processes to penetration testing and security controls. Contact your Customer Success Manager or Sales Representative to request a copy.
- Ellucian Banner
- Ellucian Ethos
- Ellucian Colleague
- Ellucian CRM
- Ellucian Insights
- Ellucian Quercus
- Ellucian Elevate
- Ellucian Experience
- Ellucian Degree Works
- Secure Code Pipeline
Compliance and Regulatory Standards
As a technology vendor dedicated to higher education, we endeavor to keep abreast of the critical standards and regulations applicable to our customers around the world. Ellucian performs rigorous testing and quality assurance of its products and services designed for these standards. For information on product updates related to regulatory compliance, visit https://www.ellucian.com/compliance-regulatory-standards.
Thought Leadership and Related Content
Visit Ellucian’s Blog to see what’s new with security-related trends, innovations, and challenges.
Featured content:
Responsible Disclosure
We take the security of our systems seriously, and we value the work of the security community. The disclosure of security vulnerabilities to Ellucian helps us keep information secure. We want to thank those of you who have helped so far by honoring you on our Security Researcher Hall of Fame.
Guidelines
We require that all researchers:
- Make every effort to avoid privacy violations, violation of licensing terms, degradation of user experience, disruption to production systems, and destruction of data during security testing
- Perform research only within the scope set out below
- Use the identified communication channels to report vulnerability information to us
- Keep information about any vulnerabilities you’ve discovered confidential between yourself and Ellucian until we’ve had 90 days to resolve the issue
- Allow an appropriate amount of time for customers to deploy updates before releasing any specific details of the issue that could harm those customers
If you follow these guidelines when reporting an issue to us, our commitment is to:
- Work with you to understand and resolve the issue quickly (including an initial confirmation of your report within 72 hours of submission)
- Recognize your contribution on our Security Researcher Hall of Fame, if you are the first to report the issue and we make a code or configuration change based on the issue
Scope
Customers wishing to perform testing of Ellucian cloud systems must notify Ellucian (via email at [email protected]) and receive confirmation prior to the start of any testing. Such testing must be limited to non-production environments.
Researchers not affiliated with a licensed Ellucian customer should contact [email protected] for additional information prior to testing.
Out of scope
Any services hosted by third-party providers and services are excluded from scope.
In the interest of the safety of our users, staff, the Internet at large, and you as a security researcher, the following test types are also excluded from scope:
- Findings from physical testing such as office access (e.g. open doors, tailgating)
- Findings derived primarily from social engineering (e.g. phishing, vishing)
- Findings from applications or systems not listed in the Scope section
- UI and UX bugs and spelling mistakes
- Network level Denial of Service (DoS/DDoS) vulnerabilities
- Brute force attacks
Please do not submit:
- Personal information
- Credit card holder data
Reporting a security vulnerability
If you believe you’ve found a security vulnerability in one of our products or platforms, please contact us by emailing [email protected]. Please include the following details with your report:
- Description of the location and potential impact of the vulnerability
- A detailed description of the steps required to reproduce the vulnerability (POC scripts, screenshots, and compressed screen captures are all helpful)
- Your name/handle and a link (website, Twitter profile, LinkedIn profile, etc.) for recognition in our Security Researcher Hall of Fame.
